HOW ARE YOU MAINTAINING REGULATORY COMPLIANCE?
GOVERNANCE, RISK AND COMPLIANCE as a SERVICE
It’s not just about preventing cyber-attacks but governing data, managing risks proactively, and ensuring compliance. A robust GRC strategy means a resilient organization, increased customer trust, and business growth.




Governance, Risk and Compliance as a Service
With security and compliance, there’s no time for the scenic route.
There are thousands of steps between you and your cybersecurity compliance goals. Let us be your guide.
Do you have the resources and expertise to establish an effective GRC program in-house? If not, we have you covered. We work closely with you to develop and implement a customized GRC strategy tailored to your specific industry, regulatory requirements, and business objectives. Automate your processes, integrate your tools, remind your staff to complete mandatory training, manage your risks and third parties while achieving and maintaining compliance to grow your business and get ready for an audit or certification.
![]()
Be continuously compliant by connecting and monitoring 35+ systems such as AWS, Azure, Office 365, and many more.
![]()
Start with customizable, expert-verified templates. Cross mapping finds the overlap between common standards to get you cruising through compliance tasks.
![]()
Managing evidence and policies keeps everything at hand. Keep tabs on risks and vendors too. No more spreadsheets and scattered documents.
![]()
Everyone on the team needs to contribute to compliance. In this personalized portal they can access policies and handle any tasks they need to do.
![]()
Automated monitoring
The eyes and ears of a comprehensive program.
Be continuously compliant by connecting and monitoring 35+ systems such as AWS, Azure, Office 365, and many moreTemplates and cross mapping
Get a jumpstart on multiple frameworks.
Start with customizable, expert-verified templates. Cross mapping finds the overlap between common standards to get you cruising through compliance.
![]()
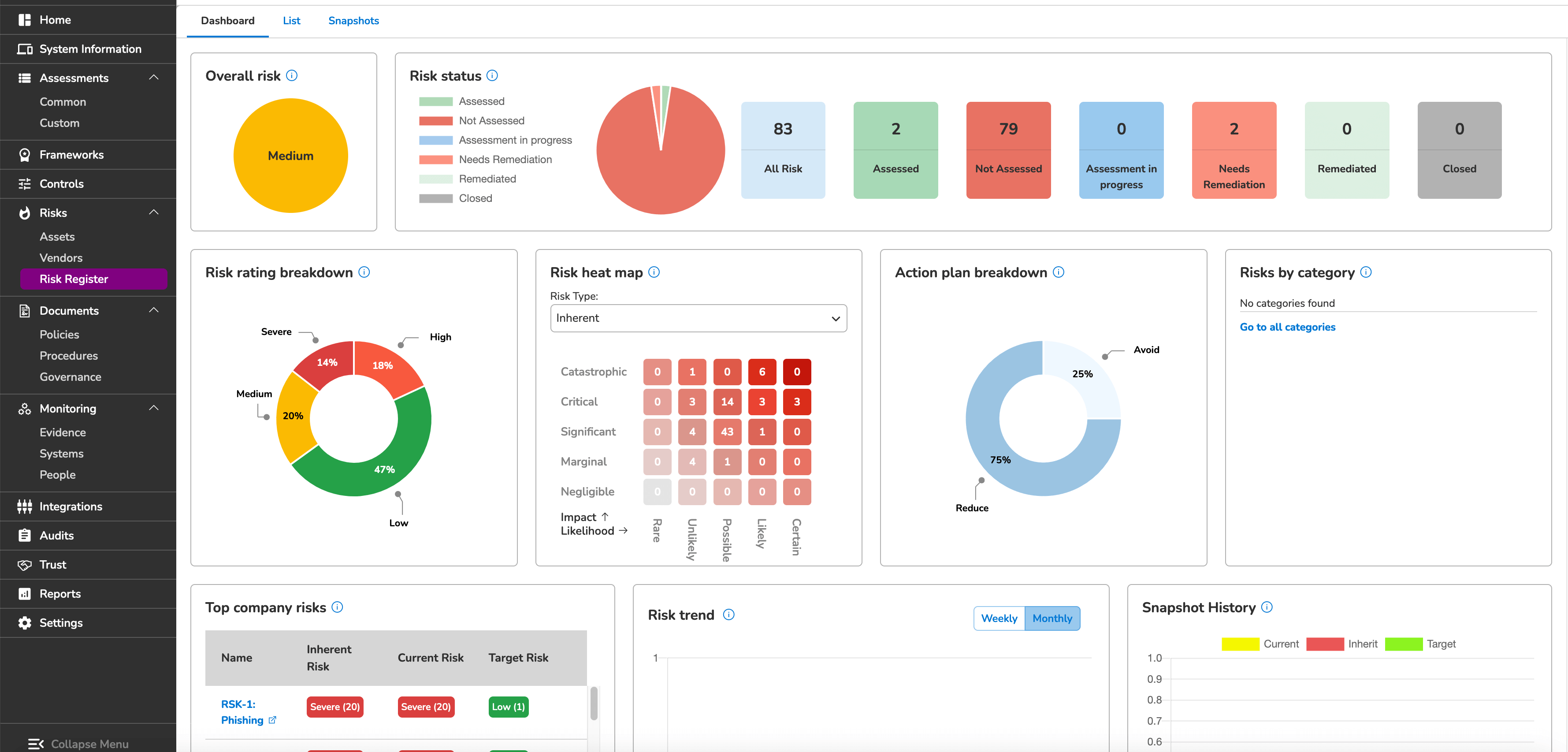
Evidence, policy, risk, and vendor management
Organized? Yes. Ready for an audit? Double yes.
Managing evidence and policies keeps everything at hand. Keep tabs on risks and vendors too. No more spreadsheets and scattered documents.
![]()
ADDRESS YOUR NEEDS

Key Features and Benefits
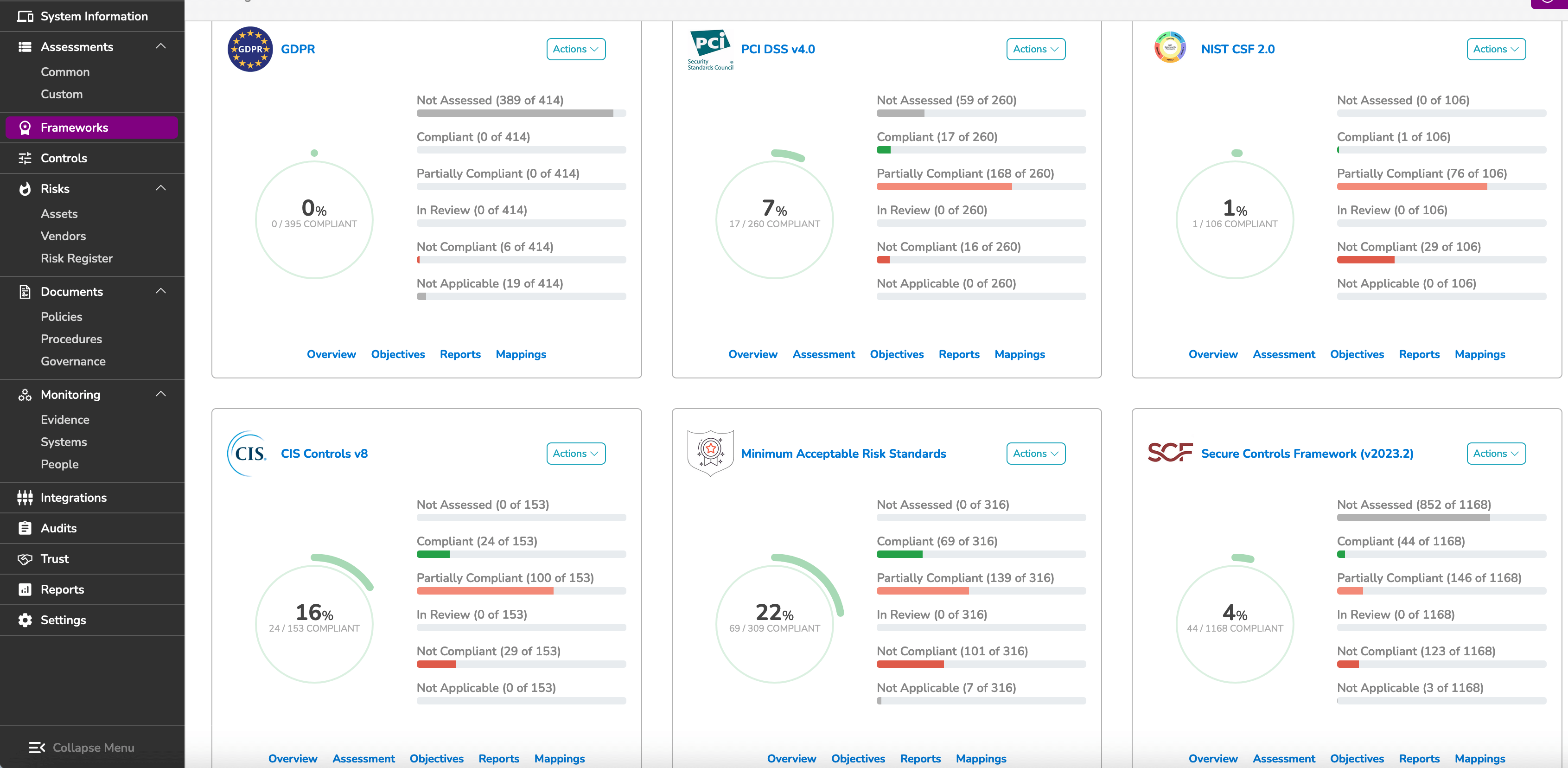
50+ Cybersecurity Frameworks Supported
SOC 2 Type I & II
The five trust services criteria
Developed by The American Institute of Certified Public Accountants (AICPA), SOC 2 helps organizations safeguard customer data. It includes five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy.GDPR
The European mega-mandate
Working with EU client data? Is your website accessible to EU citizens? You need to know about GDPR. With 99 distinct articles, this set of data protection regulations is one of the world’s most comprehensive frameworks to give people full control over their personal data.
![]()
CMMC 2.0
For defense contractors
The U.S. Department of Defense’s Cybersecurity Maturity Model Certification (CMMC) was introduced to ensure that all defense contractors and their suppliers use security protocols to protect sensitive defense information.
Companies handling Controlled Unclassified Information (CUI) or Federal Contract Information (FCI) must meet the CMMC requirements to do business with the DoD.
![]()
ISO 27001 (2022)
Implement and maintain an ISMS
ISO 27001 is the internationally recognized standard for implementing and managing an Information Security Management System (ISMS).
This standard is used to pass an audit, guaranteeing that a business’s security protocols are up-to-date.
![]()
CIS Controls
Cybersecurity best practices
The CIS Critical Security Controls (CIS Controls) are a globally implemented set of best practices used to boost an organization’s cybersecurity. They’re continually updated as these controls prioritize and simplify the steps needed for a strong cybersecurity defense.FTC Safeguards Rule
Rules for financial institutions
The FTC Safeguards Rule ensures that entities covered by the Rule maintain safeguards to protect customer information.
It applies to financial institutions subject to the FTC’s jurisdiction that aren’t subject to the enforcement authority of another regulator under section 505 of the Gramm-Leach-Bliley Act, 15 U.S.C. § 6805.
HIPAA
Securing personal health info
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a federal standard specifically for protected health information (PHI).
Regulated by the Office for Civil Rights, HIPAA outlines the permissible use and disclosure of PHI in the USA as set forth by HHS guidelines.
![]()
NIST CSF 2.0
The flexible add on
Updated in 2024, the National Institute of Standards and Technology (NIST) Cybersecurity 2.0 Framework is a comprehensive — yet flexible — set of standards, guidelines, and best practices.
It is meant to be implemented alongside existing security processes in any industry.
![]()
International compliance standards and frameworks
COBIT 2019 (Control Objectives for Information and Related Technologies) is the most recent evolution of ISACA’s globally recognized and utilized COBIT framework.
This comprehensive framework was developed to support understanding, designing, and implementing the management and governance of enterprise IT.
The Cloud Controls Matrix (CCM) and the Cloud Security Alliance Questionnaire (CAIQ) are a comprehensive set of security controls and practices.
Based on the CSA best practices, the CCM provides an industry-standard set of cybersecurity frameworks tailored specifically to cloud computing.
ISO/IEC 27017:2015 offers rigorous guidance on the security of cloud computing. You’ll want to follow ISO/IEC 27002 and ISO/IEC 27001 standards in addition to specific information security controls.
This code of practice gives clear instructions for additional controls based on the cloud services being used.
ISO/IEC 27701 helps organizations standardize how they handle Personally Identifiable Information (PII). By doing this, you’ll be set to comply with other data privacy regulations.
It includes guidelines on how to manage PII, making this a valuable tool for promoting data privacy within organizations.
This industry-driven initiative creates a secure foundation for cloud computing services to protect Personally Identifiable Information (PII).
Microsoft Data Protection Regulations (DPR) are annual requirements that Microsoft suppliers enrolled in the SSPA program must abide by.
This is to ensure Personal Data and Confidential Data are properly processed. All Microsoft suppliers need to adhere to these regulations.
The MPA manages security assessments at entertainment vendor facilities on behalf of its member studios.
This set of Content Security Best Practices outlines standard controls to help secure content, production, post-production, marketing, and distribution.
The Payment Card Industry Data Security Standard (PCI DSS) is essential for anyone handling credit card information. These standards are designed to protect and secure payment accounts throughout the transaction process.
All companies that accept, process, store, or transmit credit card data should be sure to abide by these standards.
Secure Controls Framework (SCF) provides organizations with a comprehensive approach to cybersecurity and privacy compliance across all operational levels.
This framework offers the guidance needed to implement and maintain internal controls in line with business objectives.
USA and state-specific compliance frameworks
The Consumer Privacy Act of 2018 (CCPA) legislation grants Californian consumers more control over the personal information businesses collect from them.
The CCPA provides directions on how organizations can comply with the law. Legal obligations include handling consumer rights requests and providing customers with necessary notices related to their privacy policies.
Criminal Justice Information Services Security Policy (CJIS) is a set of security standards created by the FBI. CJIS provides the structure needed to handle sensitive criminal justice information.
This policy is mandatory for law enforcement agencies, courts, correctional facilities, and any third-party entities that access, store, or transmit this type of data.
FedRAMP® was launched in 2011 to provide a cost-effective and risk-focused model for the federal government’s use of cloud technology.
This program is essential for government operations as it ensures that cloud technologies are implemented securely and efficiently.
The Cybersecurity Assessment Tool helps financial institutions recognize potential risks and determine their cybersecurity preparedness.
Developed by the Federal Financial Institutions Examination Council developed with ideas from the FFIEC Information Technology Examination Handbook, NIST Cybersecurity Framework, and industry-established best practices.
Minimum Acceptable Risk Standards (MARS) is designed to ensure the availability, confidentiality, and integrity of protected health information (PHI), personally identifiable information (PII), and federal tax information (FTI).
Developed by the Centers for Medicare and Medicaid Services, the standards are based on the National Institute of Standards and Technology (NIST) Special Publication 800-53.
Similar to the CMMC 2,0, NIST Special Publication 800-171 (NIST 800-171) is a federal standard that establishes procedures for defense contractors and subcontractors.
Specifically, it’s for the management of Controlled Unclassified Information (CUI), like personal data, equipment specs, logistical plans and other defense-related information.
he NIST AI Risk Management Framework (AI RMF) is designed to manage risks associated with the use of artificial intelligence, improving trustworthiness in AI systems’ design, development, and deployment.
It is vital for organizations as it offers structured guidance on integrating trustworthiness into AI operations, supporting broad AI risk management efforts through a collaborative and consensus-driven approach.
NIST created the Privacy Framework as a voluntary framework designed to help organizations protect individuals’ privacy while also creating innovative products and services.
This gives organizations the tools to better identify and manage potential privacy-related risks.
The NYDFS Cybersecurity Regulation (23 NYCRR 500) is a comprehensive set of requirements for financial institutions operating under NYDFS jurisdiction.
It covers organizations such as banks, insurance companies, and credit unions, as well as their third-party service providers, and aims to safeguard sensitive financial data.
TX-RAMP (Texas Department of Information Resources program) is a data security certification requirement for cloud computing services.
It provides “a standardized approach for security assessment, authorization, and continuous monitoring of cloud computing services that process the data of a state agency.”
Canadian Compliance Frameworks
Created for small and medium organizations seeking to improve their cybersecurity resiliency.
This framework is designed to provide a baseline, not a comprehensive (and complicated) plan. Its goal is to provide 80% of the benefit from 20% of the effort, making it easily accessible to smaller businesses.
This multi-faceted, government-led program aims to enhance cybersecurity measures across the country.
Launched by the Canadian Centre for Cyber Security in 2018, the certification is divided into five Organizational Controls and 13 Baseline Controls to address various components of cybersecurity best practices.
European Compliance Frameworks
The Digital Operational Resilience Act (DORA) is a regulatory framework aimed at strengthening the cybersecurity and operational resilience of the financial sector within the European Union.
It is critical for financial institutions as it mandates comprehensive management of ICT risks, ensuring consistent and robust security practices across the sector to prevent and mitigate cyber incidents.
IASME Cyber Assurance is designed for small and medium-sized organizations. It is a cost-effective standard that helps MSPs and their clients demonstrate the steps they are taking to protect sensitive information.
In order to implement this framework, organizations must first have a strong cybersecurity foundation and become compliant with the IASME Cyber Baseline Framework.
The IASME Cyber Baseline provides a structured approach to compliance for small and medium-sized organizations, including MSPs. This framework helps SMEs establish a strong foundation for cybersecurity compliance.
The IASME Cyber Baseline framework is recognized as one of the UK government’s Cyber Essentials schemes, emphasizing their credibility and relevance in the cybersecurity domain.
TISAX is an industry-standard method for assessing and exchanging information security for enterprises.
Companies use TISAX to simplify the process of evaluating supplier’s level of data security and determine how to handle sensitive customer information.
With two levels, Cyber Essentials and Cyber Essentials Plus, businesses can proactively protect themselves from security risks.
his framework provides the essential elements of a successful privacy management program. It’s not comprehensive and isn’t a substitute for compliance with other data protection regulations.
Make sure to consider your specific needs, and consult GDPR when necessary.
Compliance Frameworks for APAC
The Australian Energy Sector Cyber Security Framework (AESCSF) is the result of a collaborative effort between several government and industry stakeholders.
This framework is designed to ensure the highest level of security in the energy sector.
Australian organizations of all sizes must defend themselves against malicious cyber threats. To assist organizations with defending against cyber threats, the Australian Cyber Security Centre (ACSC) created the Essential Eight.
This is a baseline of key mitigation strategies as defined by ACSC’s Strategies to Mitigate Cyber Security Incidents.
This Prudential Standard is designed to help ensure that APRA-regulated entities have the capability to safeguard themselves against information security incidents (including cyberattacks).
They are required to maintain information security that matches the threat posed by digital vulnerabilities.
The Protective Security Policy Framework (PSPF) outlines the Australian Government’s protective security policy. It provides guidance on how to effectively implement the policy in four key areas: personnel, physical, governance, and information security.
With the PSPF, government organizations are able to ensure effective security measures.
The New Zealand Information Security Manual provides essential controls and processes necessary for protecting all New Zealand Government information and systems.
The manual also provides additional controls to help you exceed the minimum acceptable baseline levels.
TRAINING & COMPLIANCE
- Policy Management
- Cyber Training
- Weekly Security Shorts
- Dark Web Monitoring
- Simulated Phishing
TECHNICAL RISKS
- Security Scanning
- Vulnerability
- Assessment
- Network Scanning
- Web Scanning
- Technical Assessment
- Remediation
- Recommendation
FUNCTIONAL AND BUSINESS RISKS
- Mapping to:
- Regulations
- Standards
- Domain
- Industry
compliance frameworks and standards supported
prebuilt risk templates for common risks
audit-ready templates for policies, procedures, and governance documents
integrations to automate evidence collection
Integrations
Primary Integrations

Discover more integrations


Clients Testimonials
No more chasing people to deliver evidence, automated reminders for employees to complete their training, sign policies, no more missed
Thomas A.
Great tools. Much better than managing spreadsheets and gives management an instant overview what our risk and compliance status is.

Robert Bruce
We have the fully managed service and it exceeded all our expectations. Professional, efficient, and truly transformative for our business!

Cassie Ventura
We have multiple audits per year and with the full automation and the managed service we work on items as

Kate Kingston
Outstanding experience from start to finish. This saves us so much time across so may departments. The automation piece is

Sam G.
Flexible Pricing Plan
Advanced Compliance and security Risk Assessment Service is an enterprise-grade assessment and management service for those who are serious about compliance! Get your access to manage your compliance and your personal virtual and fractional CISO to answer any questions you have.
Contact us

